-
On this page
Part 1: Executive summary
1.1 This report presents the findings of the Office of the Australian Information Commissioner’s (OAIC) privacy assessment of Data Zoo, GBG greenID and Nexigen Digital. We examined their open and transparent management of personal information in their roles as Gateway Service Providers (GSPs) in the Document Verification Service (DVS).
Why we did this assessment
1.2 The OAIC’s Digital ID regulatory strategy outlines how we intend to use our regulatory powers to build trust and confidence in Australia’s Digital ID System and make ID verification in Australia more secure and privacy protective. The DVS is a key pillar of the identity verification system—both in its own right, and in support of the Australian Government’s Digital ID System (AGDIS). The Attorney-General’s Department (AGD) is the government agency with Commonwealth responsibility for identity and biometrics, and administers and operates the identity verification services, including the DVS.
1.3 A GSP is a private organisation that has a direct connection to the DVS that allows other government and non-government users to connect to and use the DVS. The DVS checks whether the biographic information on identity documents matches the original record. The result will simply be ‘ yes’ or ‘no’.
1.4 Business users (who do not have their own direct connection to the DVS) use GSPs, which have system-to-system arrangements with the AGD for identity matching requests. The DVS had over 121 million instances of use in 2023-24 with 2480 entities using the services: 127 were government users and 2353 were private sector users.[1]
1.5 GSPs are required to comply with the Privacy Act.[2] Unlike entities accredited under the Digital Identity Act, they are not required to adhere to additional privacy safeguards.
1.6 Given their important role in the identity verification ecosystem, the OAIC assessed GSPs to examine whether their privacy policies reflected open and transparent flows of personal information handling between the customer, business users and the GSP.
Objective and scope
1.7 The assessment focused solely on the identity and document verification process the GSPs offered. It assessed whether their service offerings as a GSP were accurately reflected in their privacy policies in relation to the collection, use and disclosure of personal information, including to and from third parties.
1.8 Specifically, the assessment examined the privacy policies in relation to the entities’ GSP services, to identify whether they contained the information required under APP 1.3 and 1.4, and that the policies indicated the GSPs had underlying practices, procedures and systems in line with APP 1.2.
Key findings, risks and recommendations
1.9 We found that 2 of the 3 GSPs (Data Zoo and GBG greenID) predominantly complied with APP 1.3 and 1.4. Their privacy policies demonstrated transparency around receiving and disclosing personal information to and from third parties for identity verification purposes. The remaining GSP (Nexigen Digital), which provided the DVS connection for its own subsidiaries ( not other business users), did not reflect its GSP service in its privacy policy.
1.10 The assessment identified 7 privacy risks:
- 2 high risks (Nexigen Digital) relating to the privacy policy lacking reference to the GSP use of personal information for identity verification processes
- 1 medium risk (Data Zoo) relating to a lack of detail about its complaints handling process in its privacy policy
- 2 low risk (Data Zoo and GBG greenID) relating to readability and structure of the privacy policies
- 1 low risk (GBG greenID) relating to the retention period of sensitive information collected in the identity verification process and its inclusion in the policy; and
- 1 low risk (GBG greenID) relating to the specificity in the policy for retention timeframes of sensitive personal.
1.11 This resulted in 3 recommendations and 4 suggestions:
- 2 recommendations (Nexigen Digital) to update their policy to include their identity verification processes to comply with APP 1.4(a)-(g)
- 1 recommendation (Data Zoo) to include a complaints handling process in its policy to comply with APP 1.4(e)
- 2 suggestions (Data Zoo and GBG greenID) to consider using a layered approach to their privacy policy to improve readability to improve their compliance with APP1.3
- 1 suggestion (GBG greenID) to amend the default setting for the retention of images to immediate deletion; and
- 1 suggestion (GBG greenID) to update their privacy policy to specify the retention periods of sensitive information to strengthen their compliance with APP1.4(b).
Part 2: The Australian Government’s identity verification ecosystem
2.1 Identity verification is the process of proving that an individual’s identity is genuine. To help facilitate identity verification, the Australian Government—in partnership with state and territory governments—has developed an identity ecosystem that provides individuals with the ability to digitally verify their identities using government-issued identification.
2.2 One of the foundations of this ecosystem is the DVS, which allows agencies or organisations to verify the biographic information (e.g. name, address, date of birth) in a government-issued identity document presented by an individual. The DVS verifies this biographic information against the original record held by the Commonwealth, state or territory government agency that issued the document.
2.3 The DVS verifies that the information provided matches an authentic identity document, providing a simple ‘ yes’ or ‘no’. To submit a DVS request, users to not need to provide biometric information, however the GSPs may collect this information as part of unrelated services they offer.
2.4 The Digital ID system builds on the DVS and similar facilities to create a reusable digital identity credential (such as the ATO’s myID) as shown in figure 1.
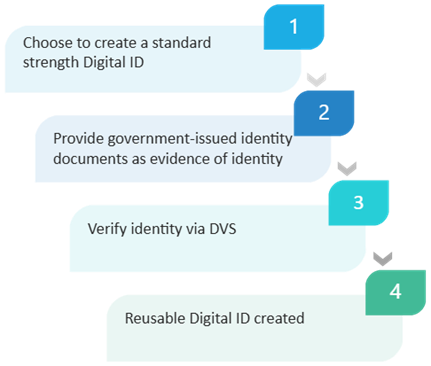
Document Verification Service
2.5 The DVS has operated since 2009. At the time of this assessment, it was being used by more than 2,600 government and private sector organisations.[3] AGD operates the DVS hub, as well as 2 other identity verification facilities.
2.6 A GSP is a private organisation that has a direct connection to the DVS. They have system‑to‑system arrangements with AGD for identity matching requests to be made and received, as shown in Figure 2 below.
2.7 Government and private-sector organisations (collectively referred to as ‘business users’) must either access the DVS through an approved GSP, or establish a direct connection with the DVS. Most DVS business users use a GSP to verify the identity of individuals.
2.8 Unlike the Digital ID system—where entities go through a thorough accreditation process and additional, legislated privacy safeguards apply to them—DVS participants such as GSPs are regulated solely by the Privacy Act. AGD, as operator of the DVS, also sets contractual terms and conditions for GSPs to access the DVS.
2.9 This assessment focused on GSPs that provided business users access to the DVS.
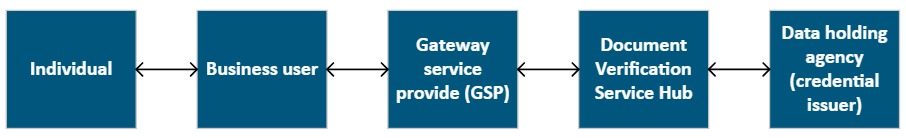
Source: OAIC analysis
The OAIC’s Digital Identity regulatory strategy
2.10 The OAIC’s Digital ID regulatory strategy[4] describes how we propose to use our regulatory powers to build trust and confidence in Australia’s Digital ID System and make identity verification in Australia more secure and privacy protective.
2.11 This strategy outlines that in the long term our activities will support outcomes including:
- all organisations enhance their privacy compliance practices and transparency
- enhanced data handling industry standards.
2.12 This assessment aims to help achieve these outcomes.
Part 3: Summary of findings
3.1 This assessment focused on GSPs as they play an integral role in the document verification process by connecting business users who need to verify the identity of individuals with the DVS. Individuals should be able to understand how the GSPs handle their personal information.
3.2 We reviewed the privacy policies of 3 GSPs to ensure they were openly and transparently handling the personal information of individuals whose identities were being verified. The 3 GSPs were:
- Data Zoo
- GBG
- NexiGen.
3.3 For each GSP, we cross-referenced their privacy policies against the privacy policies of 3 of their business users to ensure the flows of personal information between the business user and the GSP were transparent in line with APP1 requirements. Nexigen Digital’s only business user was a subsidiary business, Synergy Wholesale. It did not have any other business users.
3.4 Where required, we obtained additional information from the GSPs during the assessment.
Findings, recommendations and suggestions
3.5 The findings of the individual assessment reports are outlined below. Overall, the assessment made 7 findings: 2 high risks, 1 medium risk and 4 low risks (see Annexure D for risk ratings):
3.6 The high risk findings both related to Nexigen Digital:
- one findings was because Nexigen Digital’s privacy policy did not reflect Nexigen Digital’s management of personal information in its role as GSP
- the other findings was because the privacy policy did not have the specific information required by APP 1.4 (such as the purposes for which it collects, holds uses and discloses personal information, and information about its complaints handling process.
3.7 The medium risk was in relation insufficient information in Data Zoo’s privacy policy about its complaint handling processes.
3.8 The low risks related to:
- providing a layered approach to their privacy policy to assist readers (Data Zoo and GBG)
- excessive default retention periods for biometric information (GBG)
- specifying the retention periods in the privacy policy (GBG).
3.9 We made recommendations for the entities to address the high and medium risks, and suggestions for entities to address the low risks. Entities accepted all recommendations and 3 suggestions.
3.10 The suggestion that was not accepted was for GBG to change its default setting for the retention period for the photos it used to verify identity, from 31 days to zero days. The OAIC made this suggestion because data minimisation is better privacy practice and reduces risks for organisations. Data minimisation works on the principle that risks can be reduced by minimising the personal information collected, used and retained by an organisation.
Part 4: Background
4.1 On 6 November 2024, the Office of the Australian Information Commissioner (OAIC) notified 3 Gateway Service Providers (GSP) we were commencing an assessment under section 33C of the Privacy Act 1988 ( Cth) (Privacy Act). Section 33C of the Privacy Act provides the Information Commissioner with the power to assess whether an entity is maintaining and handling personal information in accordance with the Australian Privacy Principles (APPs).
Objective and scope of the assessment
4.2 As noted above, this assessment aims to support the OAIC’s long term Digital ID regulatory outcomes including:
- all organisations enhance their privacy compliance practices and transparency
- enhanced data handling industry standards.
4.3 The objective of the assessment was to determine whether the GSPs, in their capacity as GSPs in the Document Verification System, were openly and transparently managing personal information in line with APP 1. The objective of APP1 is to ensure APP entities manage personal information in an open and transparent way.
4.4 We did this by examining their privacy policies to ensure it contained the information required under APP 1.
4.5 The scope of the assessment focused on GSP’s compliance with APP 1, with specific focus on APPs 1.3 and 1.4:
- APP 1.3 requires an APP entity to have a clearly expressed and up-to-date privacy policy
- APP 1.4 sets out information that the privacy policy must contain.
4.6 The assessment also examined the privacy policies to identify whether they indicated the GSPs had underlying practices, procedures and systems in line with APP 1.2.
4.7 AGD, as operator of the DVS, sets Access Policy and Guidelines and terms and conditions for GSPs. [5] As these are contractual arrangements between AGD and GSPs, the OAIC has not assessed whether the GSPs comply with those arrangements.
Methodology
4.8 During this assessment we conducted:
- a desktop review of the documents the GSP provided in response to our request for information, including their privacy policies, supporting documentation such as manuals, and the list of business users
- fieldwork interviews with the staff responsible for privacy and the gateway service provision
- a desktop review of any further information provided to us as part of this assessment.
4.9 This assessment did not evaluate the operation of the GSPs policies, procedures and systems.
Assumptions and Caveats
4.10 Our assessments are ‘point in time’; that is, our observations and opinions are only applicable to the time period in which we undertook the assessment.
4.11 This report is not an endorsement of the GSPs we assessed.
Annexure A: Data Zoo
Overview
4.12 The OAIC assessed Data Zoo as having a privacy policy that largely met the requirements of APPs 1.3 and 1.4, and its privacy policy indicated it had underlying practices, procedures and systems in line with APP 1.2. [6]
4.13 The OAIC identified one medium risk and one low risk . The OAIC made one recommendation about updating its privacy policy to include how Australians can make privacy complaints and how such complaints will be managed, and one suggestion to layer its privacy policy to increase accessibility to readers.
4.14 The privacy policies of 3 of the Data Zoo’s business users reflected disclosure to third parties for identity and document verification purpose, thus demonstrating open and transparent flow of information between the business users and GSP. Data Zoo as the GSP was not identified by name explicitly in the business users’ privacy policies (this is not a stipulated requirement), but the process for using a third party for identity and document verification purposes was specified, thus ensuring open and transparent disclosures of the personal information.
Good practices
4.15 The OAIC identified the following areas of good practice for Data Zoo’s privacy policy:
- Data Zoo’s privacy policy had separate sections for each of the relevant stakeholder groups: website visitors, customers (predominantly business users) and verification subjects. This made it easy to navigate the policy and to understand how each group’s personal information was processed.
- Except for providing information about complaints, which was detailed in a separate policy (titled Dispute Resolution), Data Zoo’s privacy policy was compliant with the specific requirements applying to privacy policies contained in APPs 1.3 and 1.4.
Findings, recommendations and suggestions
The following table outlines the risks and issues in relation to the complaints process and readability that could be addressed to improve Data Zoo’s Privacy Policy and privacy practices..
APP requirement | Finding | Recommendation / Suggestion | Data Zoo response |
|---|---|---|---|
Privacy complaints Australian Privacy Principle 1.4(e) requires that an APP privacy policy of an APP entity must contain information on how an individual may complain about a breach of the Australian Privacy Principles, or a registered APP code (if any) that binds the entity, and how the entity will deal with such a complaint. | Medium risk Data Zoo’s privacy policy provided limited information about the right of Australians to complain about a breach of their privacy or how Data Zoo would deal with such a complaint. Information about complaints was outlined in the privacy policy for persons governed by the General Data Protection Regulation (citizens of the UK or those found in the European Economic Area). While the privacy policy linked to a webform that enabled a complaint to be made, the policy itself should describe the process for handling complaints, outline the process for complaining to an external complaint body (such as a recognised dispute resolution scheme) and describe the different stages in the complaint handling process. The OAIC noted that this information was available to the public through Data Zoo’s Dispute Resolution Policy available on its website. | Recommendation 1 Data Zoo should amend its privacy policy to include information about how Australians can make complaints, and how such complaints will be handled by Data Zoo. | Acceptance: Data Zoo have a standalone dispute resolution policy and complaints avenues available on our website that is available to visitors of our website and users of our service. Additionally, a dedicated category for complaints is available on our support channel for our customers. Timeframe for action: We accept this Finding and can easily address it through a summary of our complaints process as a standalone section within our Privacy Policy. We will do this in the next iteration of the Privacy Policy that we anticipate publishing on our website in June 2025. |
An APP privacy policy must be clearly expressed Australian Privacy Principle 1.3 requires that a privacy policy must be clearly expressed. The OAIC’s Guide to developing an APP privacy policy explains that a privacy policy must be easy to understand. Indicators that a privacy policy is easy to understand include:
One way to improve the accessibility and readability of a privacy policy is to take a layered approach. For example, for online publications this could include providing a condensed (summary version) of key matters in the privacy policy, with a link to the full policy. [7] | Low risk We observed that Data Zoo’s privacy policy was well structured, particularly through using headings by categories of clientele (website users, customers and data verification subjects). However, the policy contains technical content and is long at over 7,500 words, making it less accessible to some persons who have their personal information collected, used and disclosed by Data Zoo. | Suggestion 1 Data Zoo consider taking a layered approach to its privacy policy by providing a summary of key information that is easy to understand and links to its full privacy policy. | Acceptance: We accept this observation and will take it into consideration in reviewing and updating our Policy. We accept that not all the content is relevant nor required by everyone interacting with our business. We will look at creating a short version that summarises our policy and provides a link to the full policy. Timeframe for action: We will endeavour to include this high-level version with the next iteration that we anticipate publishing on our website in June 2025. |
Annexure B: GBG Pty Ltd
Overview
4.16 The OAIC assessed GBG as having a privacy policy that mostly met the requirements of APPs 1.3 and 1.4, and its privacy policy indicated it had underlying practices, procedures and systems in line with APP 1.2.[8]
4.17 We identified 3 low privacy risks. We made 3 suggestions to improve GBG’s privacy practices. The suggestions focused on layering the policy to make it more accessible to readers, clarifying its retention period for biometric information, and reducing its default retention period for biometric information.
4.18 GBG as the GSP was not identified by name explicitly in the 3 business users’ privacy policy, (this is not a stipulated requirement). The business users’ privacy policies reflected the disclosure of personal information to a third party for verification purposes.
Good practices
4.19 The OAIC identified the following areas of good practice:
- GBG’s privacy policy was well structured through the use of headings, which allowed readers to navigate quickly to relevant information
- GBG’s privacy policy outlined its practices, procedures and systems for managing personal information
- GBG’s privacy policy was compliant with the specific requirements applying to privacy policies contained in APPs 1.3 and 1.4.
Findings, recommendations and suggestions
The following tables outlines the risks and issues in relation to readability, retention default periods and specificity of retention times that could be addressed to improve GBG’s Privacy Policy and privacy practices.
APP requirement | Finding | Recommendation / Suggestion | GBG response |
|---|---|---|---|
An APP privacy policy must be clearly expressed Australian Privacy Principle 1.3 requires that a privacy policy must be clearly expressed. The OAIC’s Guide to developing an APP privacy policy explains that a privacy policy must be easy to understand. Indicators that a privacy policy is easy to understand include:
One way to improve the accessibility and readability of a privacy policy is to take a layered approach. For example, for online publications this could include providing a condensed (summary version) of key matters in the privacy policy, with a link to the full policy. [9] | Low risk Overall, GBG’s privacy policy was well structured. However, the policy contains technical content and is long at over 6,500 words, making it inaccessible to some persons who have their personal information collected, used and disclosed by GBG. | Suggestion 1 GBG could consider taking a layered approach to its privacy policy by providing a summary of key information that is easy to understand and links to its full privacy policy. | Acceptance: We were pleased that the OAIC assessed GBG as having a privacy notice that fully met the requirements of APPs 1.2 to 1.4. We have addressed the OAIC’s good practice suggestion, and this action is complete. Actions to be taken in response to the recommendation/suggestion: GBG has revised its privacy notice. The new version went live on 01 April 2025. It has been written with the user in mind, so a fourteen-year-old could understand it and easily navigate through it. We have used simple language, with clear explanations of our products and services. We also included a side menu, so the user can locate information they require quickly and easily. While we have simplified the privacy notice, it is global and needs to comply with other applicable privacy laws, such as GDPR. This inevitably adds to the length. The revised notice is available here: https://www.gbg.com/en/products-and-services-privacy-policy/ Timeframe for action: Complete |
The collection, use, disclosure and destruction of sensitive information The collection, use, disclosure and destruction of sensitive information Australian Privacy Principle 1.2(a) requires an APP entity to take reasonable steps to implement practices, procedures and systems to ensure compliance with the APPs. APP 11.2 requires that if an APP entity holds personal information about an individual, and the entity no longer needs the information for any purpose for which the information may be used or disclosed, then the entity must take such steps as are reasonable in the circumstances to destroy the information or to ensure the information is de-identified. | Low risk At the time of assessment, the privacy policy we reviewed referenced both greenID (its product used to connect to the DVS) and a product called IDScan. IDScan verifies whether a photo of an individual matches the photo on an identity document they provide. GBG advised that IDScan’s default retention period for images was 31 days. (It deleted biometric data used in the matching process immediately.) Business users could elect to reduce this retention period. Defaulting to the maximum retention period potentially results in retaining personal information longer than necessary. Defaulting to a shorter period, and requiring business users to actively extend the retention periods if needed, is a better privacy practice. Minimising data retention periods is a proactive step in reducing the quantity of personal information an organising is handling. | Suggestion 2 GBG could amend the default setting for the retention of IDScan images to deleting them immediately. | Acceptance: Not Required Actions to be taken in response to the suggestion: Biometric data is deleted immediately. For images, the default retention period is not significant (up to 31 days). Customers have the ability to reduce the retention period today. It’s important to note that, in GBG’s view—and based on customer feedback—a zero-day retention period for images would not be beneficial. This approach would prevent customers from managing enquiries related to an individual’s verification journey and eliminate the ability to effectively troubleshoot issues. Timeframe for action: N/A |
An APP privacy policy must contain information about how the entity collects and holds personal information Australian Privacy Principle 1.4(b) requires a privacy policy to contain information about how the entity collects and holds personal information, including sensitive information. | Low risk GBG’s privacy policy indicates that it retains biometric information (a ‘selfie’) and ID documents scanned for the purposes of identity verification until either:
During the assessment GBG advised that the retention period for biometrics and document image scans in IDScan is 30 days. | Suggestion 2 GBG could amend its privacy policy to explicitly reflect its retention period of 30 days (or shorter if Suggestion 1 is implemented) for biometrics and document image scans obtained via its IDScan product. | Acceptance: Accepted. Actions to be taken in response to the recommendation/suggestion: GBG’s new privacy notice, which we launched on 1 April 2025, contains a link to an Australia/New Zealand addendum (using the layering approach recommended by the OAIC), which explicitly calls out the data retention period of up to 31 days for biometric information. Timeframe for action: Complete |
Annexure C: Nexigen Digital
Overview
4.20 The OAIC assessed Nexigen Digital as having a privacy policy that largely did not meet the requirements of APPs 1.3 to 1.4, and its privacy policy did not indicate it had underlying practices, procedures and systems in line with APP 1.2.[11]
4.21 The OAIC identified 2 high risks and made 2 recommendations to address these risks. These recommendations require Digital to review and update its privacy policy to add information about its practices, procedures and systems for handling personal information and to comply with the specific requirements of APP 1.4.
4.22 Nexigen Digital as the GSP was not identified explicitly in the subsidiary’s privacy policy (this was not a stipulated requirement). The business user’s privacy policy stated that it undertook verification processes which involved transmitting documents to the issuer for validation, and disclosed information to third parties in order to provide services.
4.23 The OAIC identified the following area of good practice:
- Nexigen Digital’s privacy policy was easy to understand as it did not use jargon or complex language.
Findings, recommendations and suggestions
The following tables outlines the risks and issues that must be addressed to improve Nexigen Digital’s Privacy Policy and privacy practices.
APP requirement | Finding | Recommendation / Suggestion | Nexigen Digital response |
|---|---|---|---|
An APP privacy policy must be clearly expressed Australian Privacy Principle 1.3 requires that an APP entity must have a clearly expressed and up to date policy (the APP privacy policy) about the management of personal information by the entity. | High risk Nexigen Digital’s privacy policy provided limited information about its practices, procedures and systems for handling personal information. This included no information about the personal and/or sensitive information that Nexigen Digital handles in its role as a gateway service provider. | Recommendation 1 Nexigen Digital must update its privacy policy to include information about its practices, procedures and systems for handling personal information, including in its role as a gateway service provider. | Acceptance: Accepted Nexigen Digital’s Privacy Policy has been updated to include specific details about its procedures and systems used in the collection and handling of personal information. The policy now also specifically details our role as a gateway service provider. Timeframe for action: Revisions published on 09/05/2025 |
An APP privacy policy must contain the information required by APP 1.4 Australian Privacy Principle 1.4 requires an APP privacy policy to include the following information:
| High risk Nexigen Digital’s privacy policy did not clearly include information required by APP 1.4 (except for APP 1.4(d) which was clearly included in the policy). | Recommendation 2 Nexigen Digital must update its privacy policy to address each of the requirements of APP 1.4. | Acceptance: Accepted Nexigen Digital’s Privacy Policy has been updated to clearly reference each item of APP 1.4 with the goal that searching for key words from the APP will result in finding the relevant area of the policy. Revisions published on 09/05/2025 |
Annexure D: OAIC Risk based assessments – privacy risk guidance
Privacy risk rating | Entity action required | Likely outcome if risk is not addressed |
|---|---|---|
High risks Entity must , as a high priority, take steps to address mandatory requirements of Privacy and related legislation | Immediate management attention is required. This is an internal control or risk management issue that if not mitigated is likely to lead to the following effects |
|
Medium risk Entity should , as a medium priority, take steps to address OAIC expectations around requirements of Privacy and related legislation | Timely management attention is expected. This is an internal control or risk management issue that may lead to the following effects |
|
Low risk Entity could, as a lower priority than for high and medium risks, take steps to better address compliance with requirements of Privacy and related legislation | Management attention is suggested. This is an internal control or risk management issue, the solution to which may lead to improvement in the quality and/or efficiency of the entity or process being assessed. |
|
For more information about privacy risk ratings, refer to Chapter 9 of the OAIC’s Guide to privacy regulatory action.
[1] As cited in the Identity Verification Services Act 2023 Annual Report 2023–24 | Attorney-General's Department.
[2] GSP also have to comply with Participation Agreements, Business User Terms and Conditions of Use and Access Policy and Guidelines. These are contractual obligations to be enforced by AGD if appropriate. See Business user | IDMatch.
[4] Digital ID regulatory strategy, published 26 February 2025.
[5] Gateway service provider | IDMatch – Gateway Service Provider terms and conditions agreements and Access policy and guidelines.
[6] Data Zoo’s Privacy Policy (version 3.1 of 19 November 2024) is available on its website at Privacy Policy | Global ID Verification - Data Zoo.
[7] See – Provide information in layers - Guide to developing an APP privacy policy.
[8] GBG’s Privacy Policy (as at 29 January 2025) is available on its website at Privacy Policy ANZ | Legal & Regulatory | GBG.
[9] See – Provide information in layers - Guide to developing an APP privacy policy.
[10] See GBG’s Privacy Policy, available on its website at Privacy Policy ANZ | Legal & Regulatory | GBG.
[11] Nexigen Digital’s Privacy policy (last updated 21 August 2024) is available on its website at Privacy policy - Nexigen Digital.

